- 11 Feb 2023
- 9 Minutes to read
- DarkLight
- PDF
Search Query Language
- Updated on 11 Feb 2023
- 9 Minutes to read
- DarkLight
- PDF
The search window displayed at the top of your screen allows you to search CDC items using free text. The advanced search (query language) option is also available, with context-sensitive filtering to help you quickly zoom in on specifics.
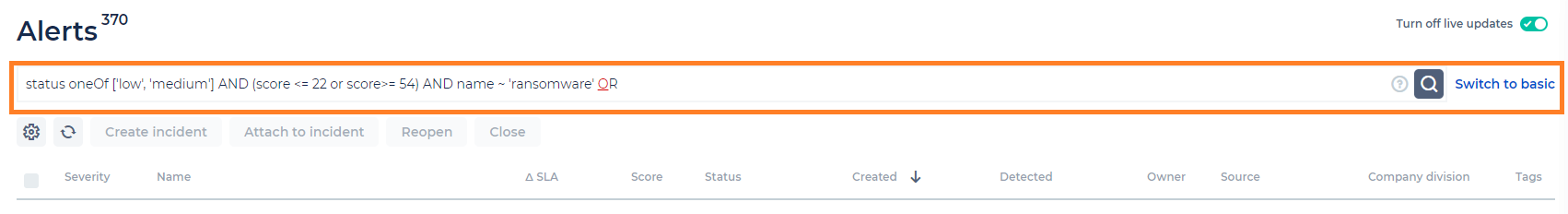
With the basic search, you can search any type of text characters throughout the CDC platform. The search is not case-sensitive. The search results are displayed below the search window in a multi-tab display, showing the number of resulting items, per type – Incidents, Alerts, Messages and Observables.
- Click the Search tab from the main menu.
- Enter the required text in the Search window.
- You must enter at least one character to activate the Search button.
- When searching incident names, complete words are required. However, a more general search term can be used to return information for the other items.
- You can use the Update button to view the most recent items, since the CDC platform is constantly refreshed every few minutes (depending on your system setup).
- Click Search.
- Clear the Search window to clear the search results or simply click the Search main menu tab.
To the right of the Search bar is a Help button (?), which you can use to open a search guide for the advanced search/query language mode. You can toggle between the basic search mode (for alerts and incidents grids), and the advanced query language search. The query language search is available in the Alerts and Incidents grids, and executed on alerts and incidents data - as well as on the related Observables and Chat.
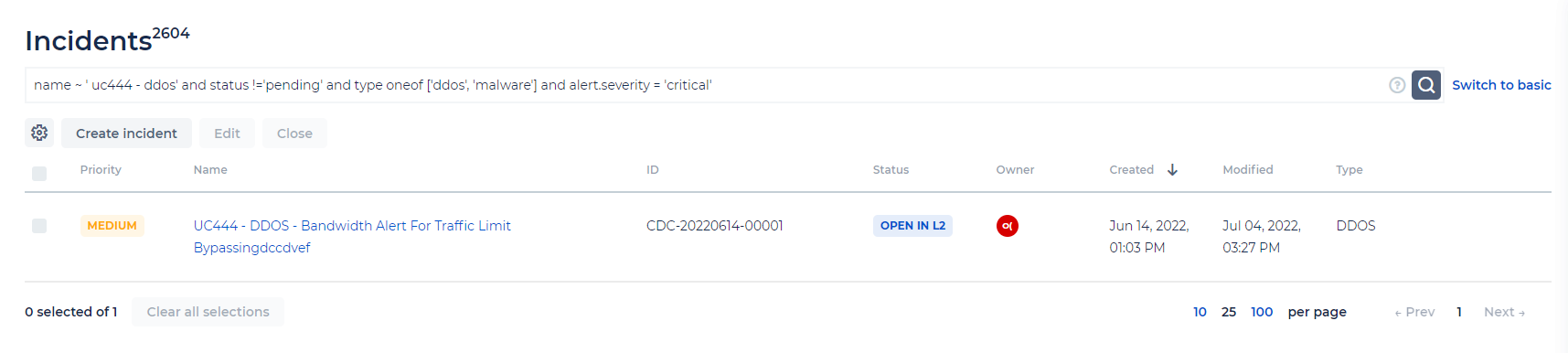
The query language search lets you search with more specified items. This search type is context-sensitive and will guide you through the relevant options as you select the required items to search.
When you click on the Switch to QL button:
- The advanced search mode is opened.
- All of the filters applied are converted to the QL search request.
You can also search by specific fields using operators and aliases (fields names), as described in the sections below.
The advanced search tool provides flexibility and efficiency, as well as multiple criteria combinations.
Example 1:
Query/Search: Severity = 'HIGH' AND ObservableTags oneof ['Tagx', 'Tagy']
Returns: All alerts with Severity = HIGH AND ObservableTag = (TagX AND/OR Tagy)
Example 2:
Query/Search: DetectionRule = 'AO10' AND Severity = 'HIGH' AND ObservableTags oneOf ['1.1.1.1','2.2.22']
Returns: All alerts with DetectionRule = AO10 AND Severity = HIGH AND (ObservableTag = 1.1.1.1 OR ObservableTag = 1.1.1.2)
Tips for Writing Queries
- User/owner should be entered as a full username in order to find it in the UI. If you enter alert.user =, you should enter the full name as two words (first name and surname, with a space between them). Note that this is not case sensitive.
- Currently, Mitre ATT&CK values can only be found by IDs. For example, mitreAttacks oneof ('T1548', ‘T1018’).
- When the status of an incident is “Pending”, you can find it by the initial group. For example, when the incident is escalated from the “Customer” to “L1” group, the current incident status is “Pending for L1”, but the search finds it by group (only group = ‘Customer’), as it is still not accepted/revoked.
- Query language supports AND/OR logical operators (joiners), which join the expressions/conditions in the query.
- After entering a parameter name, the operators can be =,!=, ~, oneOf but not <,>.
- Query language supports the following operators: = , != , <=,>= <,>, Contain (~), oneof
- Query language supports brackets () and multiple brackets ((())).
- You can search by partial value. To do so, use the Contain (~) operator.
- When searching a parameter in observables, all related alerts and incidents that are associated with the observable will be displayed.
Autosuggestions (Release 2.8 and above)
The QL search also supports autosuggestions of parameter names from a drop-down list. Autosuggestions are available for valid collections, fields, and operators when using the QL search. When clicking on the search, there will be a drop-down list with the queries that you can choose from.
Notes:
- When entering a space after the operator, the drop-down with the list of autosuggested values is shown. When selecting the value, it will have quotes automatically (except for NULL values). For non metadata-driven fields, you can start typing to get an autocomplete list (without quotes).
- When entering a space after construction with “collection.field operator value” or a closed bracket, the drop-down with a list of autosuggested operators is shown (OR, AND).
- The search follows the INCLUDES logic (not START WITH). For example, not only will "med" suggest "medium", but "diu" will suggest medium also.
- If a value is invalid (incorrect entering or syntax), it wil be highlighted in red.
- If a field allows a null value, NULL is placed into position #1 in the autocomplete list.
- Autocomplete supports string fields only. You can start entering values for string fields without quotes. You will get autocomplete drop-down values that validate until the first joiner (AND/OR logical operator).
- You can see autosuggestions for logical operators when using the QL, so that you can select the correct one from the drop-down list.
- You can click on the value from the autosuggestions list in the drop-down, so that it autocompletes the part of the entered operator.
- When logging out or refreshing, the queries will still be kept.
The CDC shows tooltips with a description of the error made in the QL. A tooltip is shown on hover in the following scenarios:
- When the collection name is invalid.
- When the field name is invalid.
- When the operator after field/collection.field construction is invalid (>=/<= for string values).
- When the operator after field/collection.field construction is unknown (does not exist/supported in/by QL).
Operators
Values for the fields should be put in single quotes. For example, severity = ‘Low’. If the value is a number, it should come without quotes. For example, score = 98.
You can use joiners and unlimited nested level via brackets. For example:
name != 'value2' AND (description != 'description_value_1' OR (status != 'closed' AND (killChain = 'Delivery' OR (source != 'source_value_1' AND (severity = 'medium' OR categories oneof ['Category_value_1', 'Category_value_1'])))))
On the Alerts page, you only need to mention the field name in the request. For example, severity = ‘Low’. If the spelling of the field name is incorrect, it will be highlighted in red. On the Incidents page, you can define only the field name if it is specific for incidents.
You can use joiners such as OR and AND in order to create complex request and combine different conditions. Example: severity = ‘Low’ OR severity = ‘High’ AND status = ‘Open’ and score >= 54
The following table details the field types, along with the operators that you can use with them.
| "<=" returns Less Than Equal | ||
| ">=" returns More Than Equal | "!=" returns Not Equal | |
| "<" returns Less Than | "=" returns Equal | |
| ">" returns More Than | “OneOf” returns One Of | "~" returns Contains |
| alert.score | alert.tags | alert.tags |
| observable.suspiciousRate | alert.killChain | alert.killChain |
| alert.categories | alert.categories | |
| alert.name | alert.name | |
| alert.description | alert.description | |
| alert.source | alert.source | |
| alert.sourceId | alert.sourceId | |
| alert.sourceUrl | alert.sourceUrl | |
| alert.severity | alert.severity | |
| alert.status | alert.status | |
| alert.score | alert.type | |
| alert.type | alert.owner | |
| alert.owner | alert.company | |
| alert.company | alert.mitreAttacks | |
| alert.mitreAttacks | alert.useCase | |
| alert.useCase | alert.threatType | |
| alert.threatType | alert.threatActors | |
| alert.threatActors | alert.malwareTools | |
| alert.malwareTools | alert.closingReason | |
| alert.closingReason | alert.observableTags | |
| alert.observableTags | incident.status | |
| incident.status | incident.type |
Fields Available for Use
Alerts:
| Search Field String | UI Field Name |
|---|---|
| tags | Tags |
| killChain | Kill Chain |
| categories | Categories |
| name | Alert name |
| description | Alert description |
| source | Source |
| sourceId | Source |
| sourceUrl | Source URL |
| severity | Severity |
| status | Status |
| score | Score |
| type | Type |
| owner | Owner |
| company | Company division |
| mitreAttacks | Mitre ATT&CK |
| useCase | Use case |
| threatType | Threat type |
| threatActors | Threat actor |
| malwareTools | Malware and tools |
| closingReason | Closing reason |
| observableTags | Tags (related observables) |
Observables:
| Search Field String | UI Field Name |
|---|---|
| tags | Tags |
| suspiciousRate | Related observable Score |
| value | Related observable Observable |
| type | Type |
Messages:
| Search Field String | UI Field Name |
|---|---|
| text | Message text |
Incidents:
| Search Field String | UI Field Name |
|---|---|
| status | Status |
| type | Type |
| tags | Tags |
| name | Incident name |
| description | Incident description |
| priority | Priority |
| group | Group |
| key | ID |
| owner | Owner |
| company | Company division |
| mitreAttacks | Mitre ATT&CK |
| users | Members |
| alerts | Alerts |
Note that when searching in the Incidents grid and using collection.field construction, and this collection is not the one where you are now (for example, if you are in the Incidents grid and search for an alert), - alert.name = ‘Ransomware’ will find all the incidents related to the alert with the name ‘Ransomware’. This is also true for chat and observables.
Examples
If you want to find alerts/incidents (depending on grid you are in currently) by specific message text, you can try the following:
- message.text = 'this alert is false positive and should be closed' – to find an exact match if you know the exact message text.
- message.text ~ 'is false positive' – to run a partial search. In this case the results will be all of the alerts/incidents that contain “is”/”false”/”positive” keywords in the messages within.
If you want to find alerts/incidents (depending on grid you are in currently) by specific observable tag/type/value/suspicious rate, you can try the following:
- observable.tags oneof ['warning', 'high_priority', 'sentinel'] or observable.suspiciousrate >= 75 or observable.value ~ '192.168.' and (observable.type != 'ipv4' OR observable.type != 'ipv6') – to find all the alerts/incidents with the observable(s) which are with the tag 'warning'/'high_priority'/'sentinel' OR suspicious rate >= 75 OR value that contains 192.168. AND type is not IPv4/IPv6.
If you want to find incidents by several conditions, you can try the following:
- priority oneof ['high', 'critical'] and message.text ~ 'reopen' and alert.severity = 'high' or alert.name = 'alert_851b9de033' – on the Incidents page, will find all the incidents with high or critical priority, with a message within that contains “reopen’, and with an alert with severity HIGH within or an alert with 'alert_851b9de033' name within.
DateTime
You can search alerts by:
- created datetime
- detected datetime
- modified datetime
You can search incidents by:
- created datetime
- modified datetime
You can search observables by:
- created datetime
- modified datetime
You can search messages by:
- created datetime
- modified datetime
Notes:
You can search by date and time - yyyy-mm-dd hh:mm
- Seconds should be ranged automatically (00-59). For example, 2022-12-01 13:05 should find 2022-12-01 13:05:00-2022-12-01 13:05:59.
You can search using different time fields in the same query. For example: creationTime < ‘2021-01-01’ AND detectionTime < ‘2021-03-03’.
You can use QL operators such as : <,> , =< , =>, =, !=, oneOf for date values.
You can add date/datetime fields as sort options to / search/advanced
Note that date fields are accounted in UTC (not in local time).
SLA
- Supports days, hours and minutes (d, h, m).
- Syntax: 5d 10h 5m
- seconds should be ranged automatically (00-59). For example, 5d should find SLA 120h 0m 0-59s. 4h should find 4h 0m 0-59s
- Supported for new alerts and incidents.
- The following are the operators that should be used with the SLA field: >, <, = (only for NULL value), and !=(only for NULL value).

