- 02 Apr 2025
- 2 Minutes to read
- DarkLight
- PDF
Alert Grouping (Admin)
- Updated on 02 Apr 2025
- 2 Minutes to read
- DarkLight
- PDF
The CDC alert grouping mechanism groups alerts together into incidents (threats). This enables security analysts to have better context of the issues they need to handle, and perform faster analysis and reduce the investigation time for similar alerts - working only with incidents that gather alerts.
For example, let's assume that two alerts are generated in two minutes. The first alert comes from the EDR with information about malware on a host, and the second alert comes from the firewall with the same host communicating with a known C&C address. The CDC will then detect these two alerts and group them together into one incident.
Alert Grouping Settings
You can set up and manage alert grouping through the Settings menu (Settings > Grouping Management).
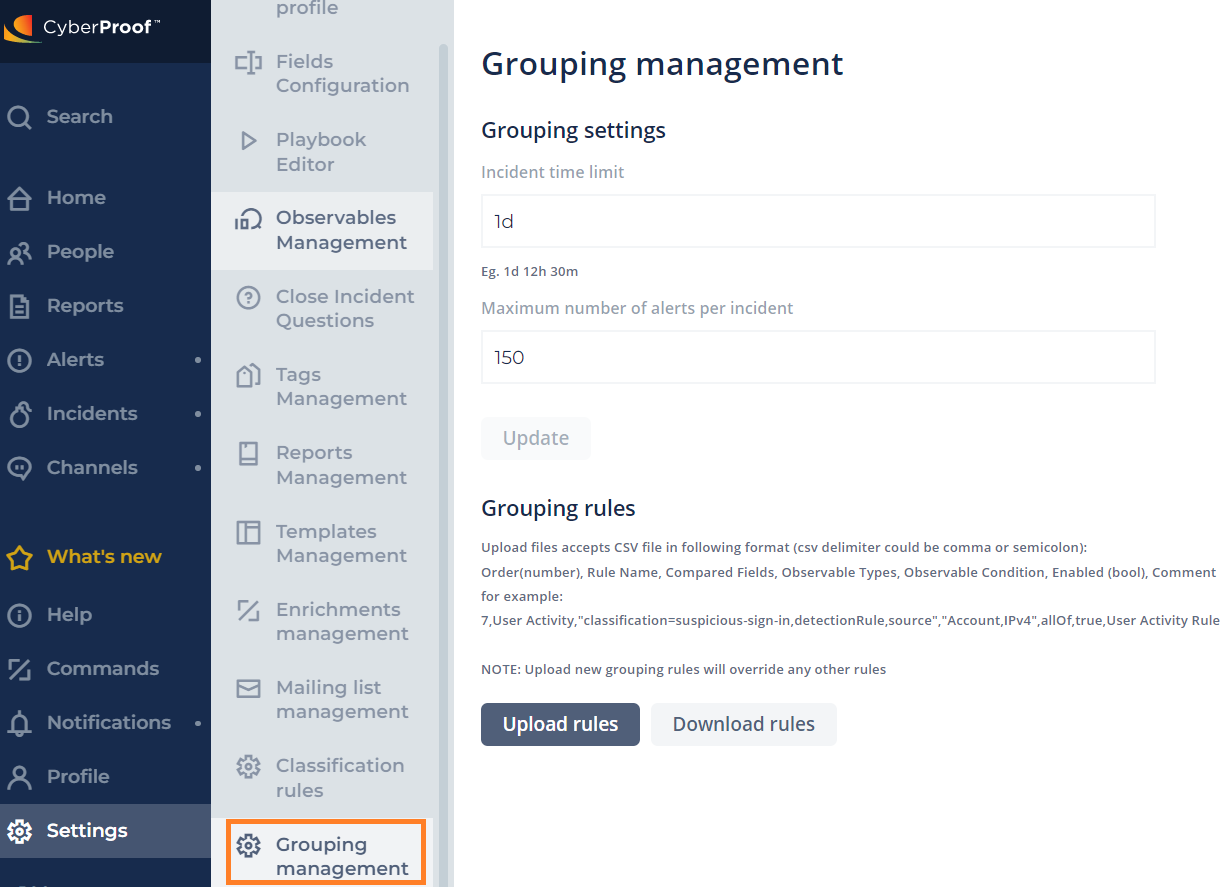
Here you can set up your incident time limit (for how long you want to attach the alert from the time the incident was created), and the maximum number of alerts that you want to have per incident.
Grouping Rules
You can set grouping rules by downloading them into a CSV file. You can configure the rules within the CSV before uploading it back to the system, in order for the rules to start to work.
In the Grouping rules section:
- Click Download rules to download the rules in CSV format. You will see the downloaded CSV in the upper right corner of your screen.
- Open the file to view the rules.
The rules for grouping are based on a heirarchal system where each incoming alert is matched against a rule. When a rule is matched, the system will stop and will not check other rules.
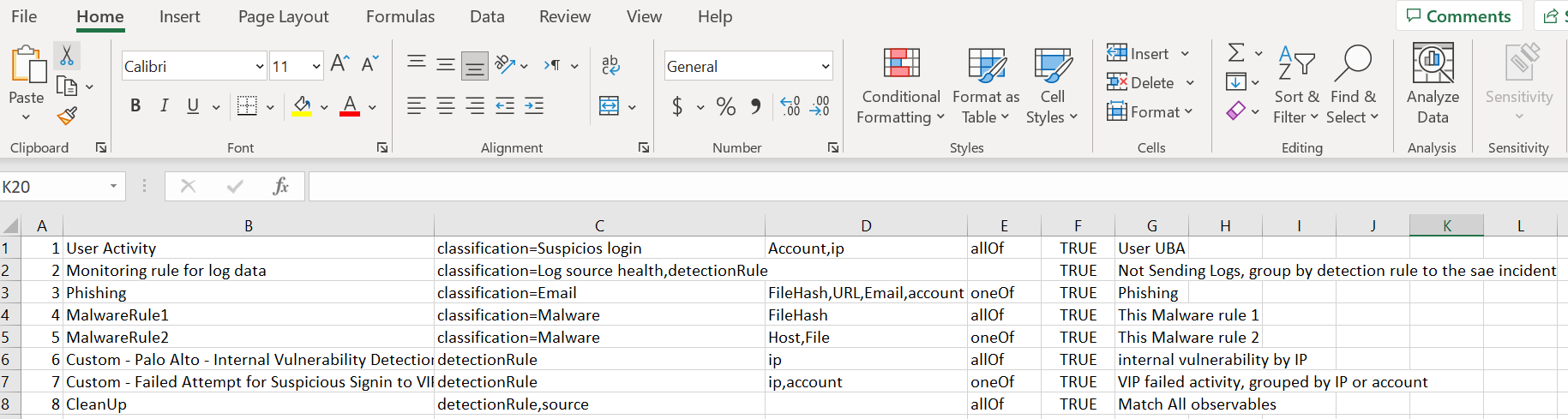
In the rules file, let's say for example that you see several alert classifications that look suspicious. You may want to group those alerts into the same classification, called "suspicious login." When doing so, all of the alerts with same classification will be grouped, even they don't have a common detection rule, source, IP, etc.
Note that in this example, if you only set the classification to be "suspicious login" in the rule file, the logic will only check alerts having that classification. If you want to group classifications with certain common observables, you will have to define the rule that way in the rules file.
Operators
The following details the rules file operators.
- Group by all observables (allOf)- all observables must be identical between an alert and an incident.
- Grouped by any observable (anyOf) - any observable must be identical between an alert and an incident.
- Group by one or more observable type (oneOf) - (with an And operator between them ) AND detection rule.
- Group by classification AND Observable type AND other fields (e.g., detection rule).
- Click Upload rules to upload the rules back to the platform.
Notes:
- Upload files accepts CSV files in the following format (the CSV delimiter could be a comma or semicolon):
Order(number), Rule Name, Compared Fields, Observable Types, Observable Condition, Enabled (bool), Comment
for example:
7,User Activity,"classification=suspicious-sign-in,detectionRule,source","Account,IPv4",allOf,true,User Activity Rule - Uploading new grouping rules will override any other existing rules.

