- 26 Jan 2022
- 4 Minutes to read
- DarkLight
- PDF
Version 2.4
- Updated on 26 Jan 2022
- 4 Minutes to read
- DarkLight
- PDF
What's new in CDC Version 2.4
November 2021
Highlights
- Threat intelligence alerts with actionable items directly in the CDC
- Refresh reports on demand
- Filter settings persistence
- Re-run enrichments on demand
- Secure files upload
- View Mitre ATT&CK details
- Additional filters and search capabilities
- CDC support detection rule
- Copy file ID
- Global search improvements
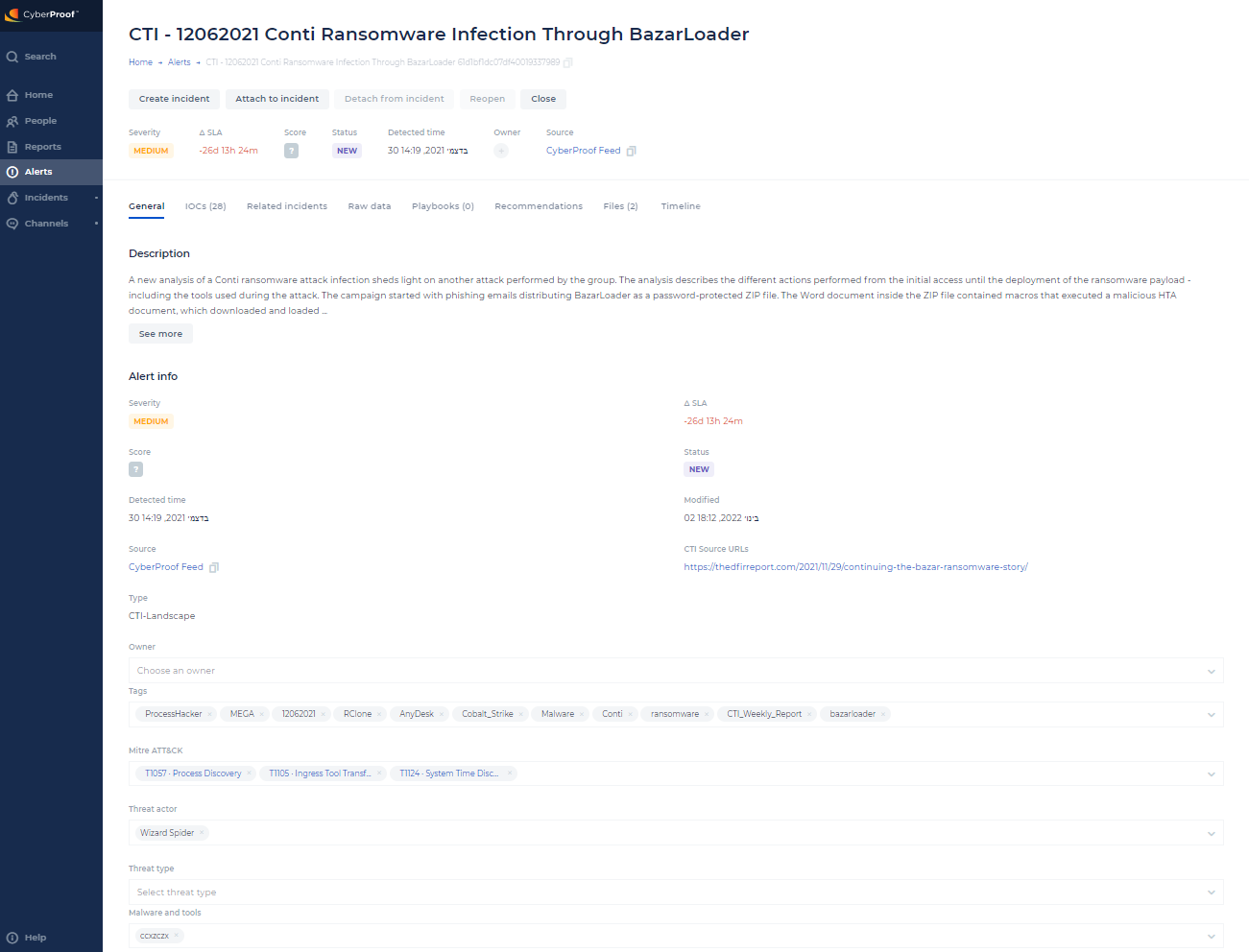
Threat Intelligence Alerts
Threats can now be reported and managed directly in the CDC platform, through CyberProof Feed.
With this capability, an L1/L2 persona can handle threat intelligence cases, as well as alerts from other sources. Using the CDC platform enables the Threat Intelligence team to gather and analyze cases using previous alert information. You will also have a view of CTI alerts and be able to see the benefits of threat prevention on your system.
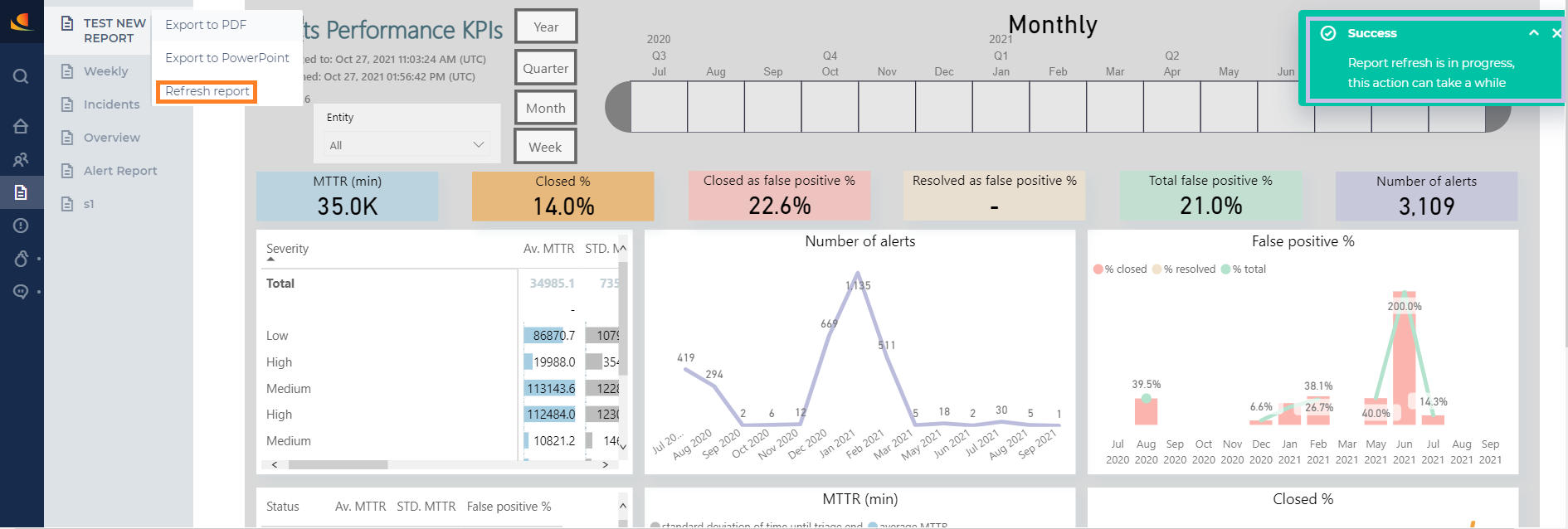
Refresh Reports on Demand
For each report, the Reports menu will now include the option to refresh a report, which will generate an updated version of the report.
This enables you to get more accurate reports and not have to wait for an automatic update.
Filter Settings Persistence
Selected filters in the Incidents and Alerts grids (and observables) will be saved even after you refresh (F5) the page or log out from the platform. You will not have to select them each time from the beginning.
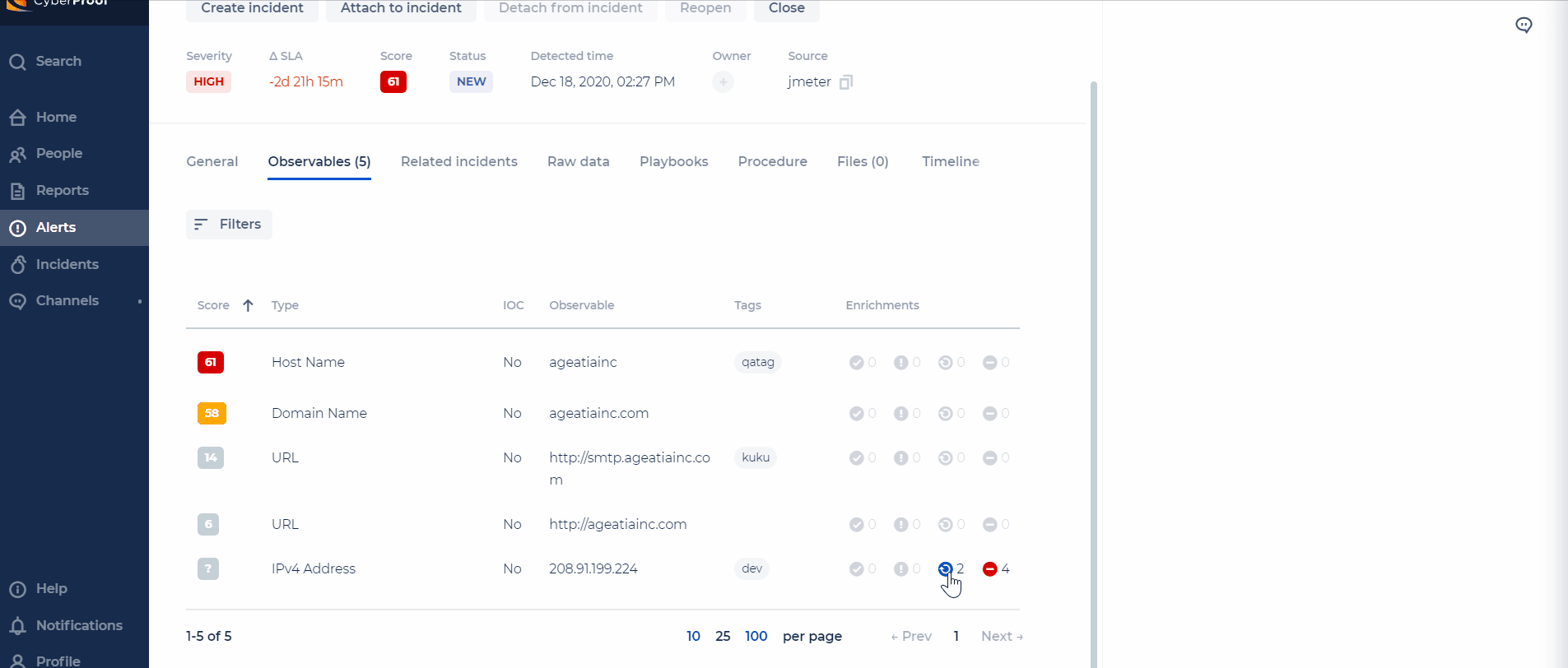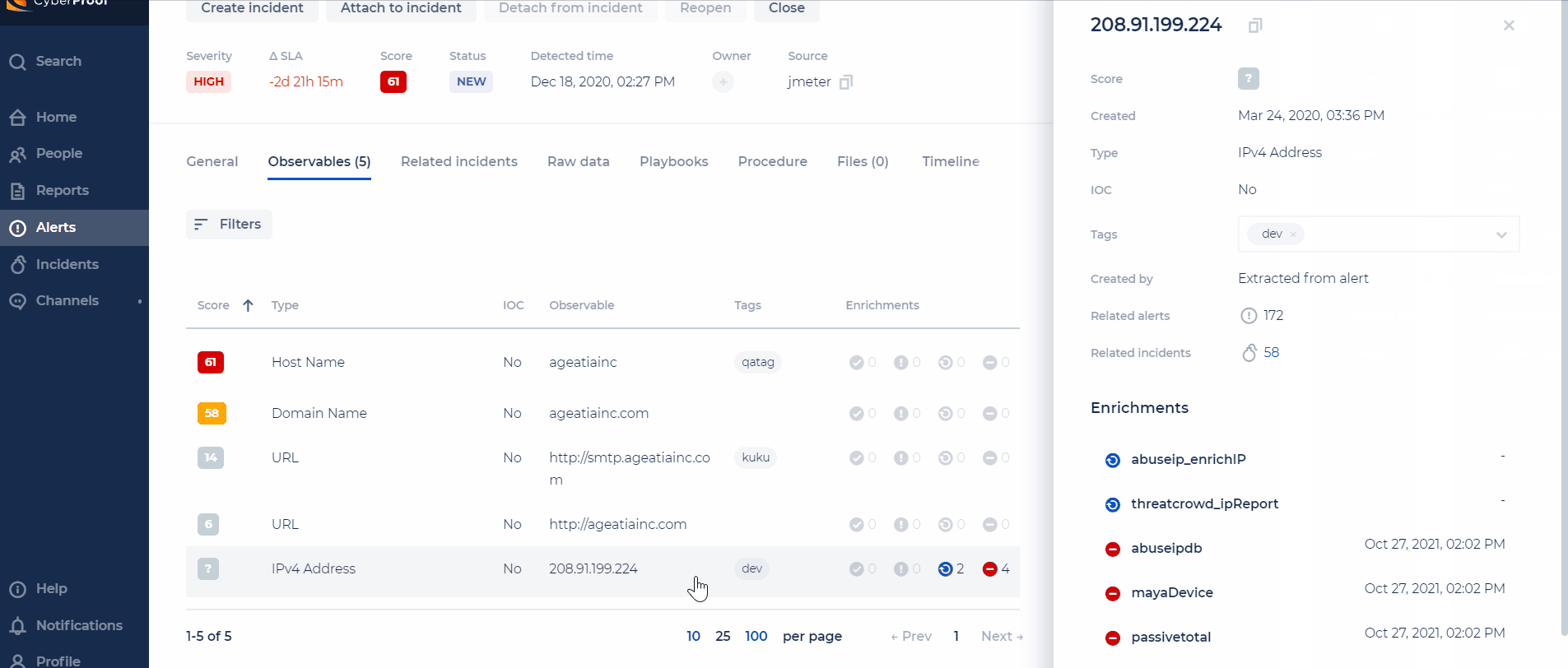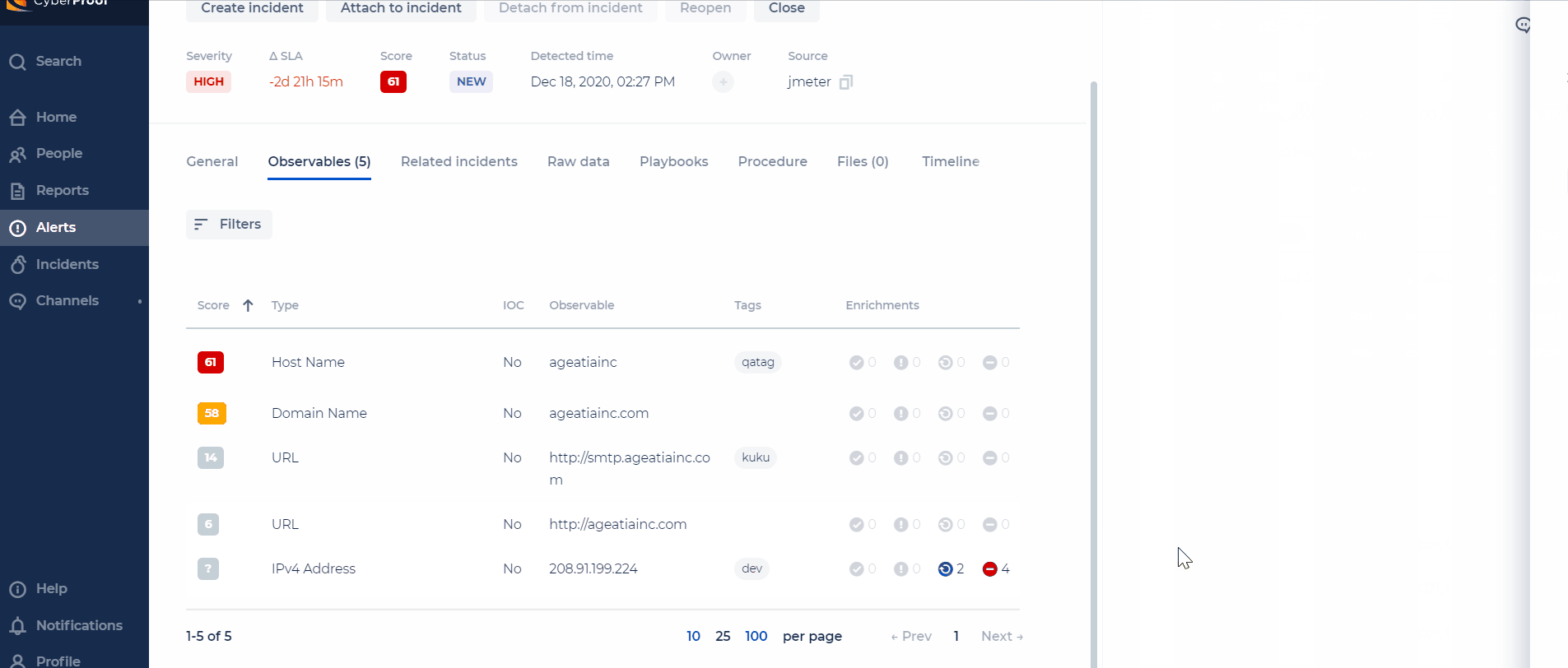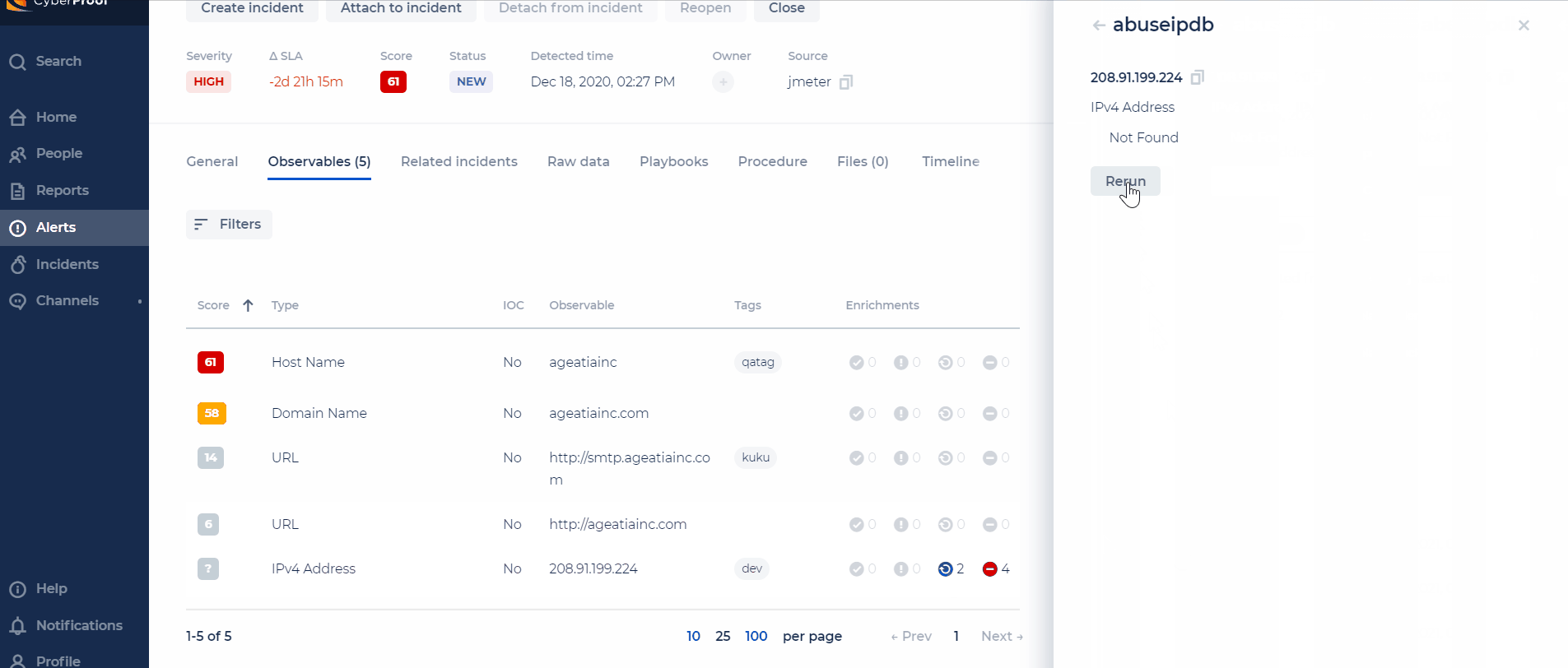
Re-Run Enrichment on Demand
For enrichments that are stuck, you can now re-run them for each observable.
Notes:
- For each enrichment source, the CDC will support a different timeout (the timeout will be configurable).
- When exciding the timeout, the status will be set to "Failed".
Secure Files Upload
Users with a role of incident/channel contributor (and above) can now upload files to the CDC. These files will be checked for malicious content. Users with these roles can also download files that were scanned before from the CDC.
Notes:
- You will not be able to download files that were not scanned.
- Password protected files currently not supported.
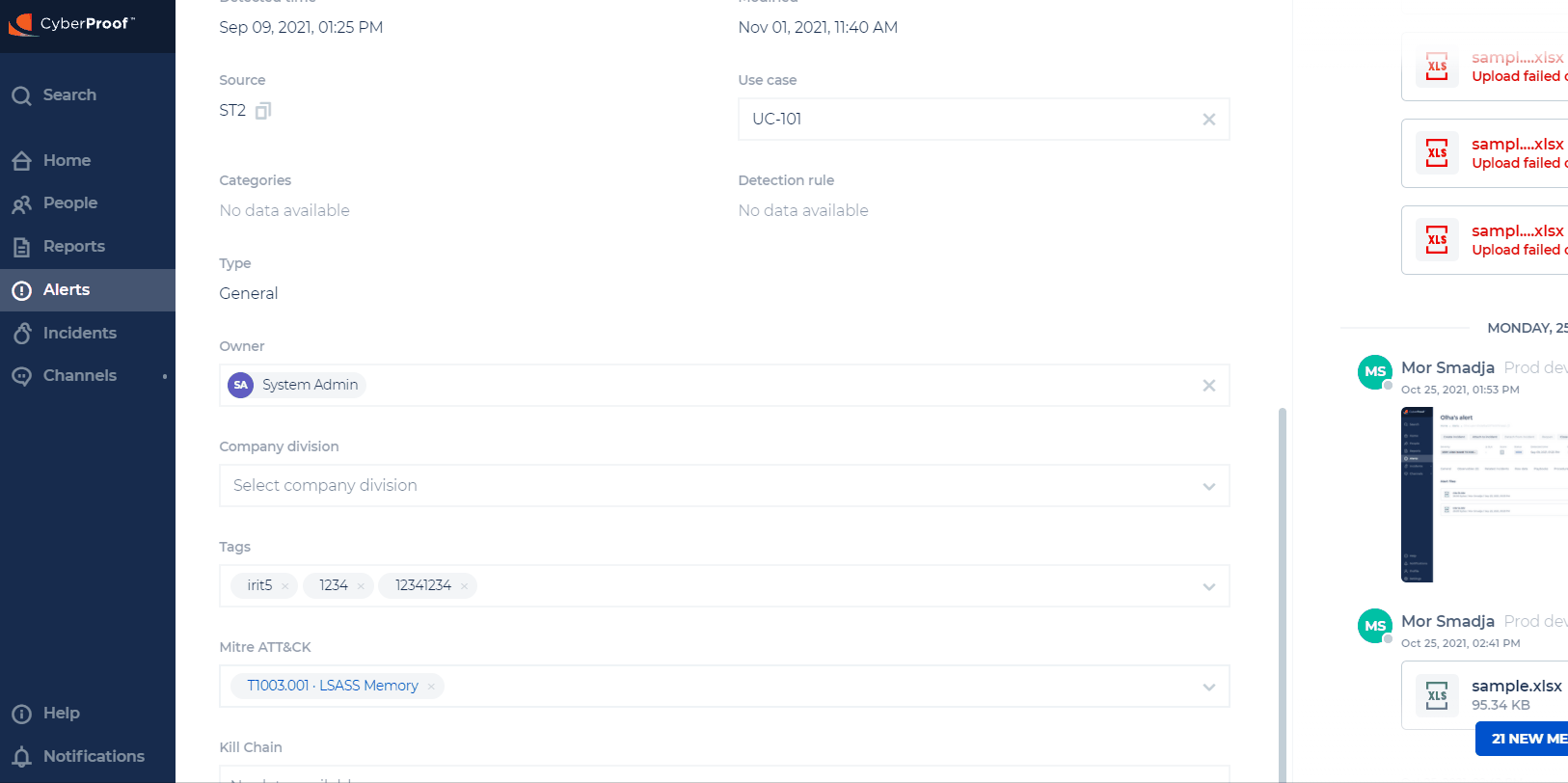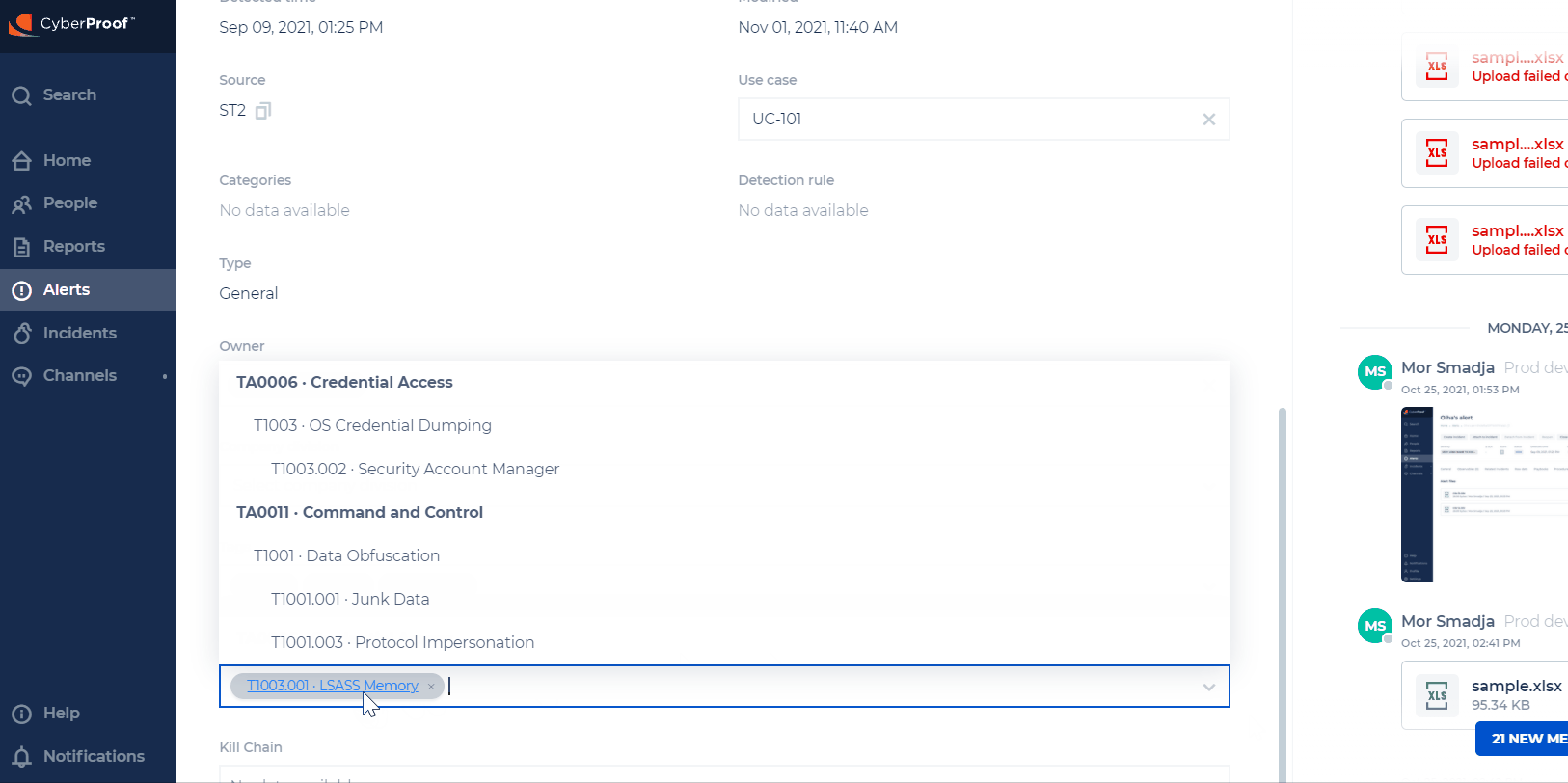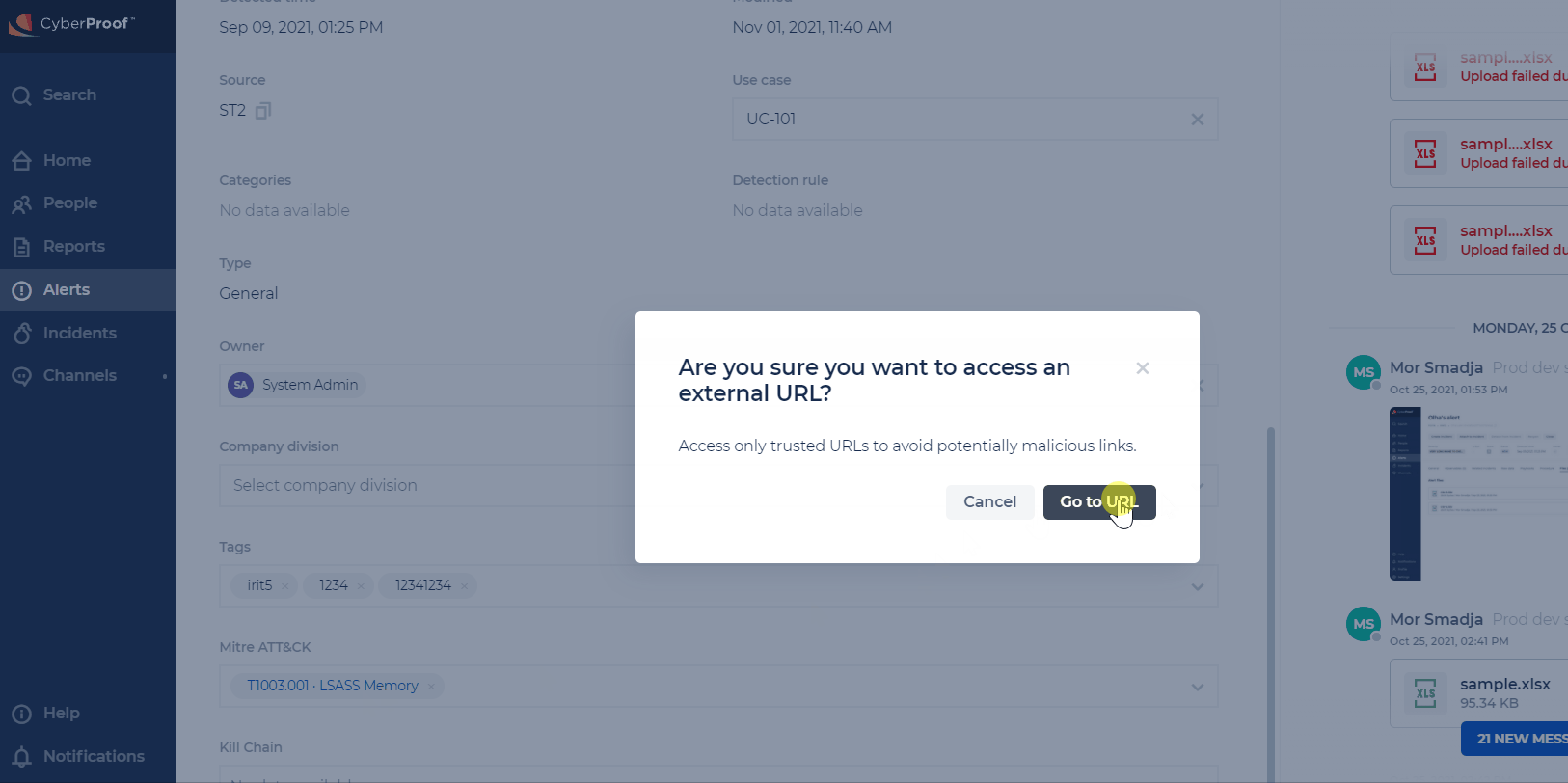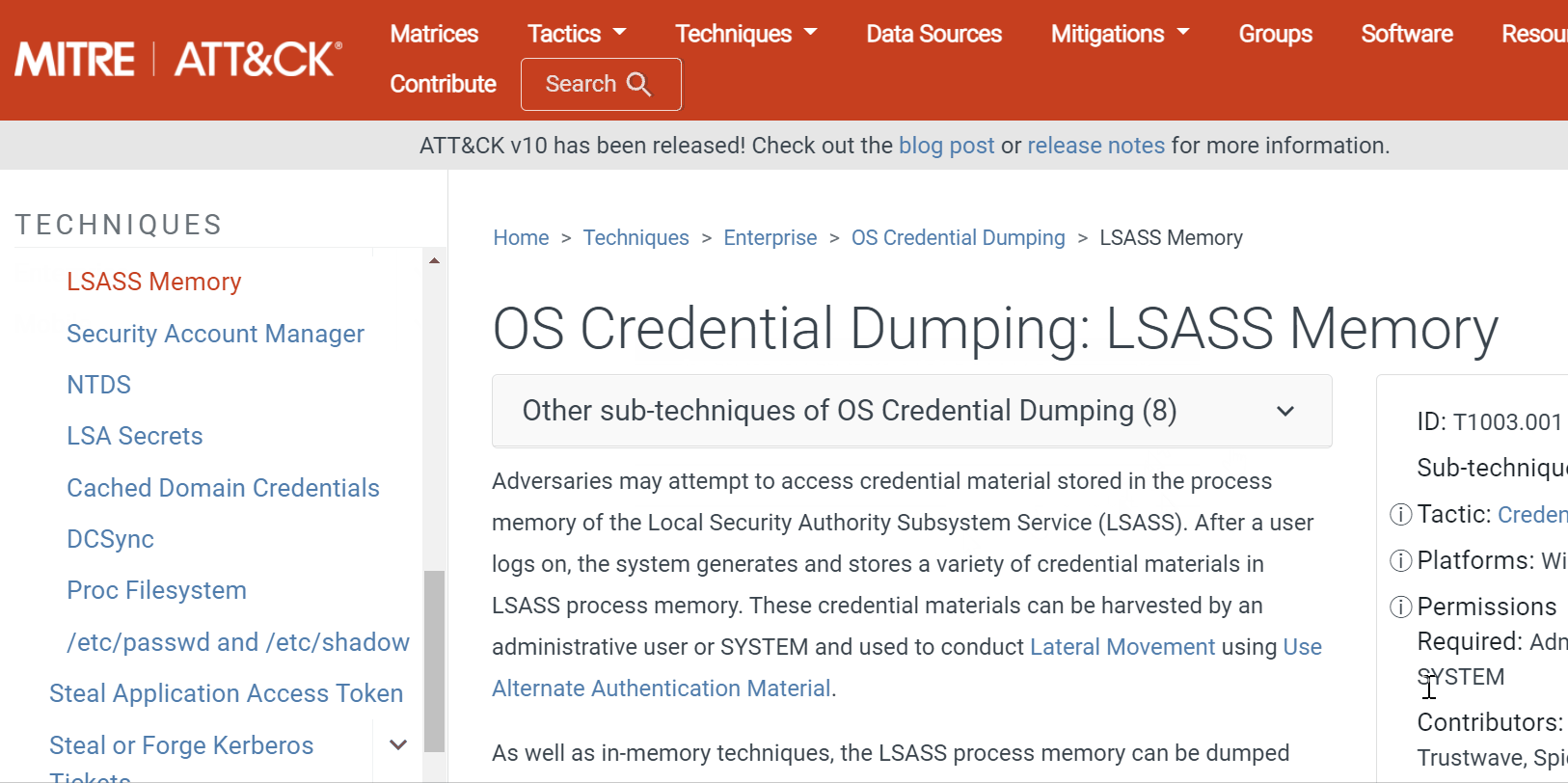
View Mitre ATT&CK Details
You can now get related Mitre ATT&CK information on alerts and incidents, so that you can better analyze and handle a case. Alerts will contain Mitre ATT&CK information such as the ID, and information on the tactic, technique, or sub-technique used in the attack.
Notes:
- The list of tactics and techniques can be changed by the Mitre organization, and the CDC will be updated accordingly.
- When a change is done in the alert, it will also be reflected in the related incident. Incidents will contain all Mitre ATT&CK information from all alerts.
- In case of a Mitre ATT&CK that is part of more than one alert and a change was done in one alert, this change will be reflected in the incident but not in the other alerts that share this information.
- Mitre ATT&CKs can be deleted and updated. The attached alerts will be updated automatically.
- When adding/updating/deleting a Mitre ATT&CK in the incident, the change will not be reflected in the attached alerts.
Additional Filters and Search Capabilities
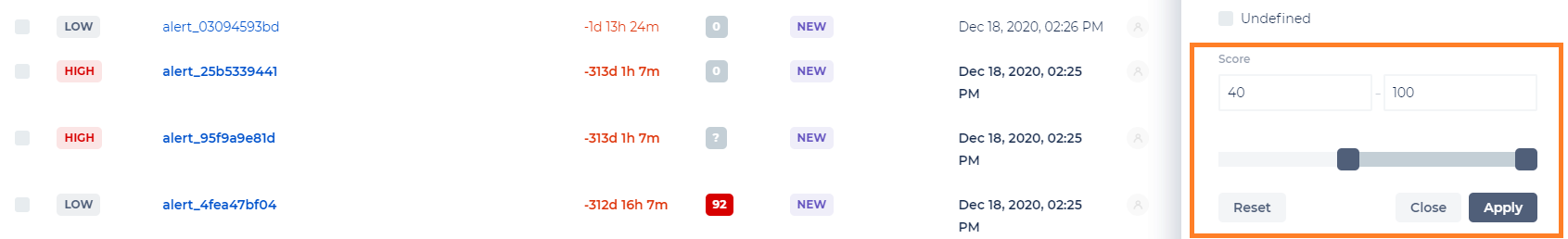
There are various new filters and search capabilities in the Alerts and Incidents grids.
These include:
- Filtering incidents by members.
- Filtering alerts by score value.
- Searching alerts by all text fields that appear in the Alerts and Incidents grids.
CDC Support Detection Rule
You can now know which alert detection rules caused an alert to be generated in SIEM or other alert provider.
When an alert is fetched, the rule name will be stored as part of the alerts data in the CDC. The Detection Rule field will appear on the Alerts Details tab. One rule can generate many alerts, but for a single alert, there can only one rule.
Note: This feature is supported in the CDC API but not in the UI.
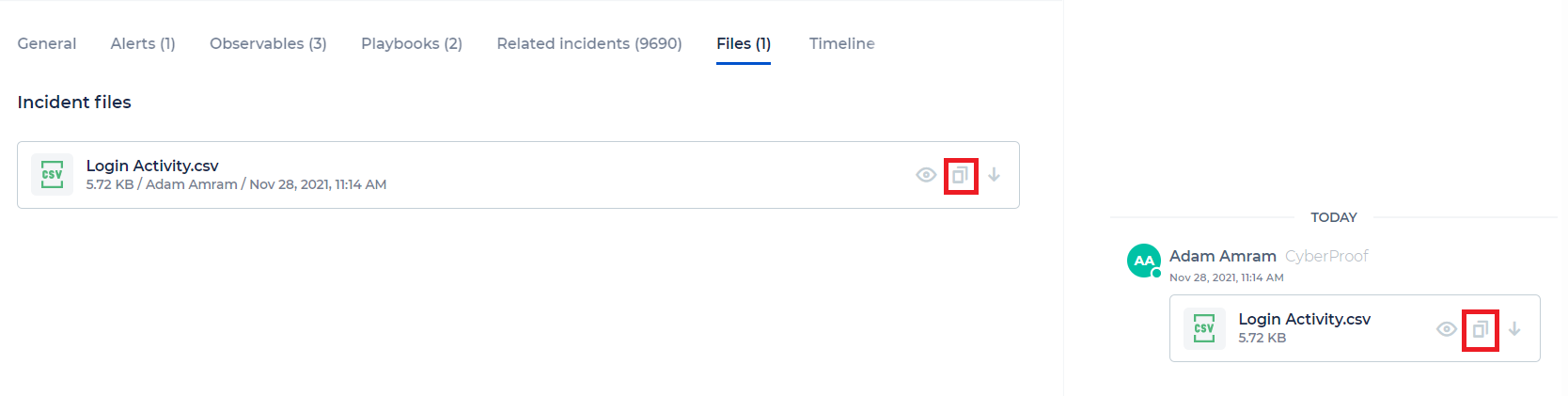
Copy File ID
You can copy the File ID in all Files appearances in the CDC: in the Files tab in Alerts and Incidents, and in chat. This is an integration that requires uploading a CSV file to an incident/alert, and then providing file details as a parameter to the CLI command.
Global Search Improvements
There are several new Global search capabilities.
These include:
- Search results - where the Incidents, Alerts, Observables, and Messages tabs show search results in various fields.
- Alerts raw data - the search now looks in the raw data as well.
- Alerts Source ID - the search now looks in the Source ID (as it is implemented in the alerts grid search).
- Saved results - the search results can be saved, so that they can be worked with once the global search is opened again during the user session.
Bug Fixes
- Playbook redirected is not working (CYB-10694).
- Incorrect message when detaching an alert from an incident (CYB-10722).
- Error when creating a new channel (CYB-10956).
- Files with brackets in the name cannot be downloaded (CYB-11306).
- Incorrect message when attaching a playbook to an alert use case (CYB-11666).
- Error in escalation email format (CYB-12022).
- Missing related alert and incidents indication of observable in the search results (CYB-12040).
Known Issues
- Search results are not saved if the search contains an unclosed date range (CYB-13389).
- Search text is not highlighted in search results (CYB-13292).
- An error will be presented if the alert description is too long while creating an incident (CYB-12360).
- Emojis in messages are shown as plain text in search results (CYB-11137).
- The Status column in related incident sorting behavior is incorrect (CYB-9650).

